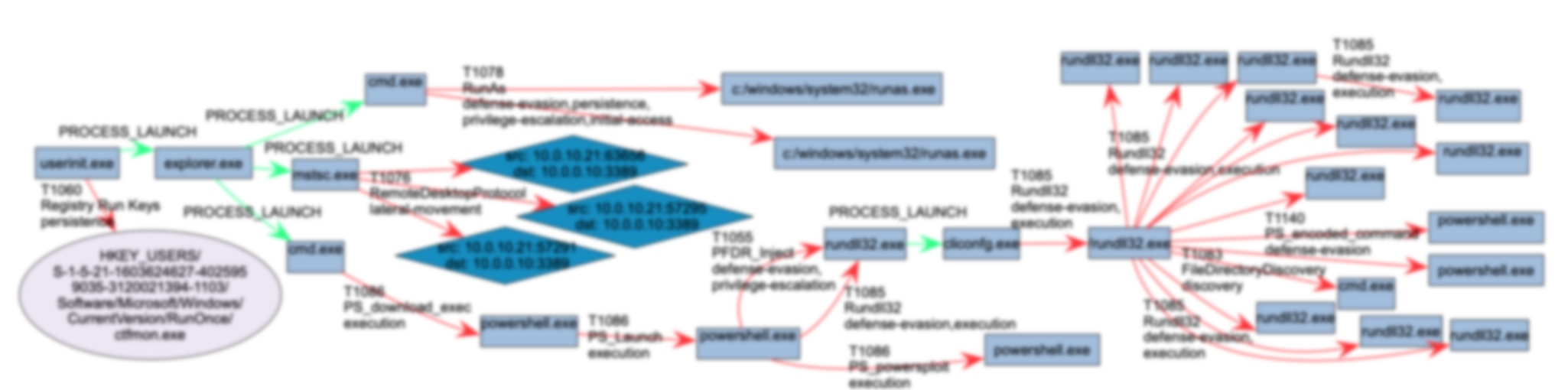
A short listing of research papers I’ve discovered recently that use Provenance Analytics for various Cyber Security usecases from EDR data analysis to malware analysis to threat hunting and IR.
- Tactical Provenance Analysis for Endpoint Detection and Response Systems
- You Are What You Do: Hunting Stealthy Malware via Data Provenance Analysis
- NODOZE: Combatting Threat Alert Fatigue with Automated Provenance Triage
- Transparent Web Service Auditing via Network Provenance Functions
- OmegaLog: High-Fidelity Attack Investigation via Transparent Multi-layer Log Analysis
- Automated Provenance Analytics: A Regular Grammar Based Approach with Applications in Security
- Mining Data Provenance to Detect Advanced Persistent Threats
- Poirot: Aligning Attack Behavior with Kernel Audit Records for Cyber Threat Hunting
–Jason
@jason_trost
The “short links” format was inspired by O’Reilly’s Four Short Links series.